Top-tier threat detection for cloud workloads
Protect your cloud workloads against unauthorized code
Top-tier threat detection with no manual configuration or overhead for your team.
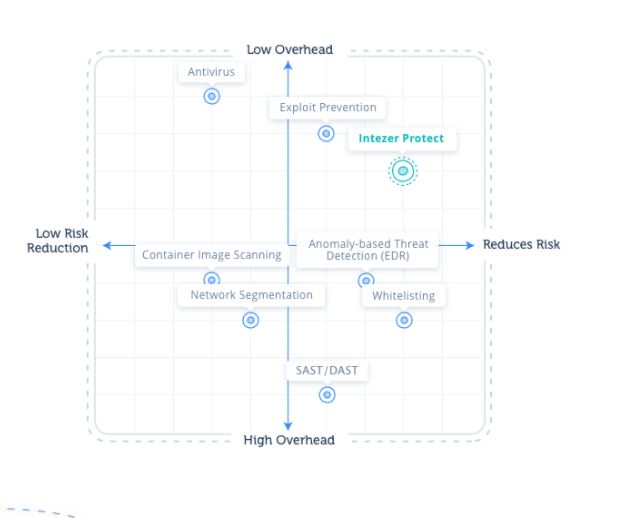
Zero Trust Execution Meets Low Overhead
The Intezer Advantage
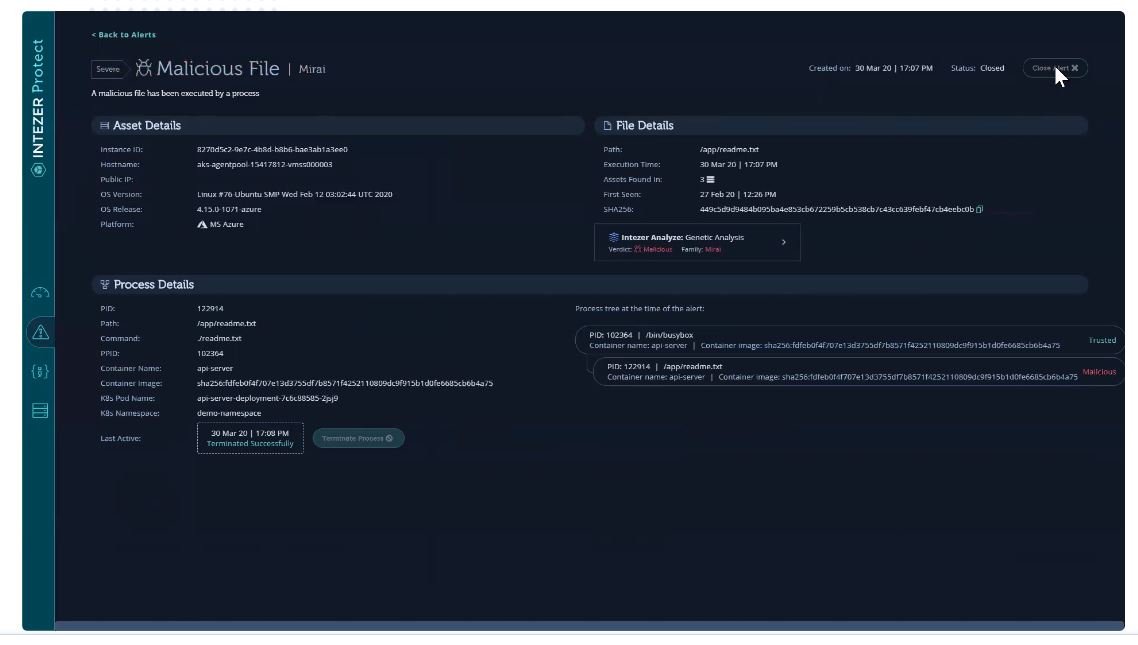
A quick win to reduce risk
Genetic Software Mapping combines a best-in-class threat detection with low operational overhead and maintenance
- Only high-confidence alerts
- No manual configuration, rules or policies required
- Seamless installation
Unprecedented visibility & control
Monitor your cloud servers in runtime to ensure that all software running on your systems is under your control—and solely from trusted origins.
Defend against modern & evolving attacks
Our in-memory Genetic Software Mapping capabilities help enterprises defend against a wide scope of attack vectors:
- Malicious code
- Vulnerability exploitation and other fileless threats
- Unauthorized or risky software
- Suspicious shell commands and administrative activity
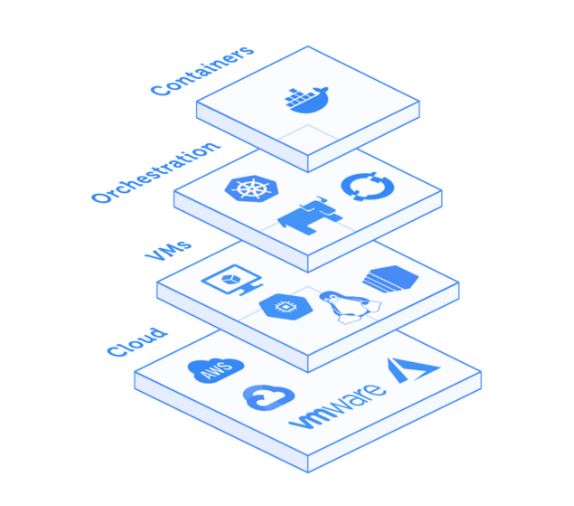
Cover the entire Cloud Native stack
Intezer Protect is designed to protect elastic, scalable and diverse cloud native infrastructure—covering the entire spectrum of your workloads.
Do you wish to know more ?