Nexus Firewall
Posted in Sonatype
Nexus Firewall
Reduce Risk. Eliminate Waste. Protect Every Application.
Create your own policy, or use one of ours.
At the heart of Firewall is the IQ Server, which provides fully-customizable policy management for identifying and protecting your repositories, as well as detailed intelligence regarding each and every component it finds.
A vigilant sentinel for your repositories.
Firewall’s Audit capabilities automatically tell you when components not meeting your policy enter your repository. Better yet this is displayed directly in your Nexus Repository Manager interface with access to detailed intelligence via the IQ Server.
Stop unwanted components at the source.
Quarantine provides your team with the tactical capability to fully prevent components from even entering a repository. But don’t worry, you can also un-quarantine and selectively permit components as necessary.
Guard not only the entry, but the exit as well.
While Firewall continuously protects your repositories, unwanted components can still sneak into your software supply chain through other means. Thus Firewall also gives you control over staging and release repositories so you can block unapproved releases from entering production.
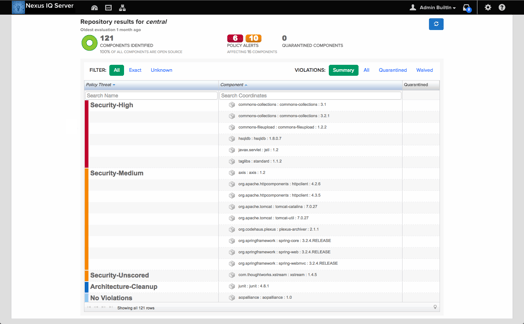
Say hello to Nexus Firewall
- Block unwanted components from entering your software supply chain.
- Empower development teams with always-on component intelligence.
- Improve application hygiene with advanced capabilities that protect repositories, including staging and release.
- Automatically monitor and prevent risky components from entering into your applications.
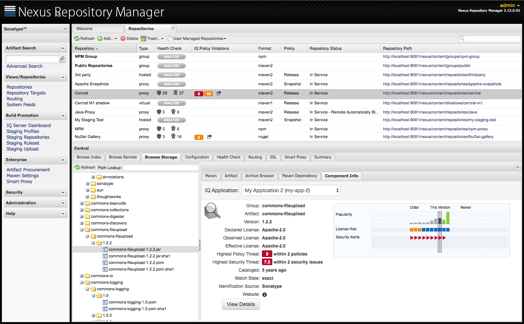
It’s all about the data
- Up-to-date and always-on component intelligence covers security vulnerabilities, restrictive licenses, component age, popularity and other quality characteristics.
- From detailed reports to the IQ Server dashboard, there are a variety of ways to digest our in-depth component intelligence.
- Intelligence directly integrated into Nexus Repository Pro means research takes minutes, not hours and days.
- Because we provide root cause analysis for security vulnerabilities, this means you won’t follow false paths or miss a dependency that could have been hidden.
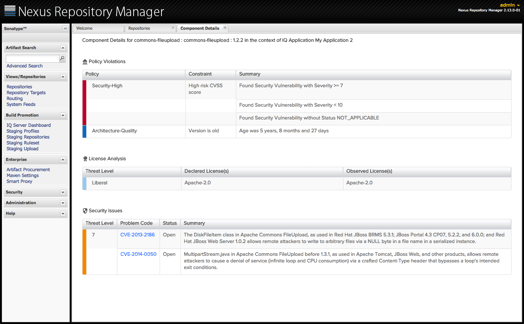
Get better data early and often
- Know which components you should or shouldn’t use, across your enterprise.
- Create policies to ensure risky components never make it into production applications.
- Not just components, but dependencies as well, are identified along with any associated security, license and quality risks
- Depending on your desired level of control, you can enable a continuous audit, or take unwanted components out of distribution with quarantine.
Do you wish to know more ?


